Understanding and Mitigating Cyber Security Risks of Working Remotely
CyberSOC Africa is closing the ever-growing gap between cyber needs and the resources to address them by training hundreds of African cyber security specialist annually - and employing the very best of them.
As a result of the COVID-19 pandemic, governments across the globe have enforced a lockdown; it becomes imperative for employees to work from a remote location, especially for companies that provide essential services. For most organizations, it may be the first time deploying remote work tools, which makes it of utmost importance to be aware of the associated risks with the remote tools such as Virtual Private Networks (VPN) and Proxies.
VPN establishes an encrypted connection (VPN tunnel) from a users’ device (VPN client) to a VPN server through the internet. A VPN as a set of technologies links computers to create a private network while another network carries the encrypted data; it establishes a connection between remote users and private networks8. It works as an extension of a private network that allows remote users to log in to a private network securely and retain access to the resources that they use on a local connection via proper encryption.
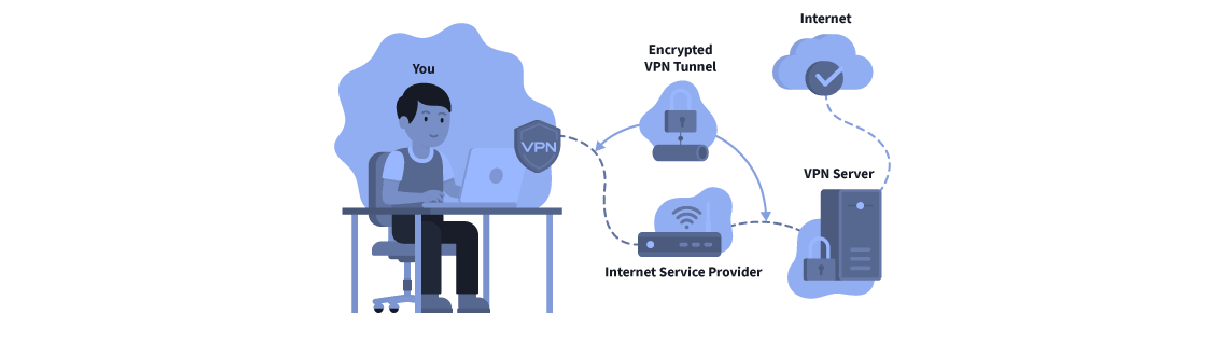
From figure 1 above, VPN ensures all the users’ internet traffic is encrypted such that it would be harder to intercept by any external party. On the users’ side, the VPN projects all connected computers as directly connected to each other.1
In computer networking, a proxy server is a server application or appliance that acts as an intermediary for requests from users seeking resources from servers that provide those resources. A proxy server thus functions on behalf of the user requesting services, masking the real source of the requests to the resource server.2
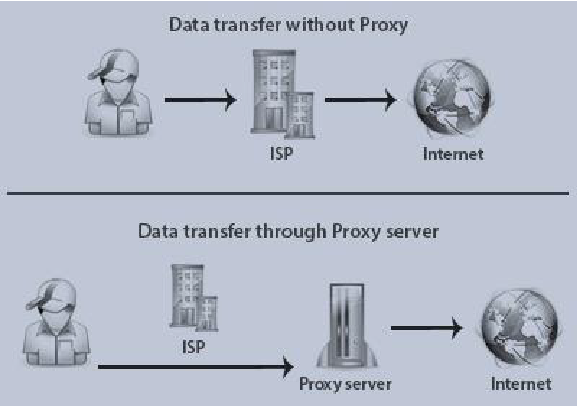
In similarities, both offer identity masking services, so users’ real identities are unknown while accessing resources.
Differences between VPN and proxy
| VPN | Are |
|---|---|
| VPN works on the Network level (operating system) of the OSI Model. It reroutes all applications and web traffic requests from any computer the VPN is configured up. | Proxy works on the Application level by rerouting the traffic from the application it is configured on (either web application traffic or others)6 |
| VPN does not stand in place of a device; it acts as a secure tunnel for transmission and access to resources | It serves as device intermediary handling requests on behalf of another host |
| Provides an additional layer of security through encryption | It does not provide an encrypted connection between source and destination. |
Cyber Security Risks of Working Remotely
The use of VPNs and proxy servers by organizations this COVD-19 period for business continuity creates more opportunities for the exploit vulnerable systems. An attacker could infiltrate a proxy faster than a VPN because VPN offers an extra layer of security in an encrypted channel that proxies do not. Therefore, while working remotely, there are certain risks associated with the use of proxy servers to access corporate network, such as:
Interception of sensitive and confidential information such as usernames and passwords of online accounts, bank, credit card details, IP address.12
Proxy providers with malicious intent can also infiltrate users’ sessions with viruses and spam through a lot of pop-up advertisements, which a user may negligently click on or download.
Mitigation of Cyber Security Risks
Organizations need to eliminate vulnerabilities linked to these tools by ensuring the software, browser, and systems initiating the connections are up to date. For VPN-related cyber incidents, breaches can be as a result of management issues in domain security for authentication and authorization systems, carelessly leaving a terminated employee enabled or systems running vulnerable software while connected to a VPN; these can give attackers access to private networks. Deployments of VPN can be complicated; therefore, to provide appropriate levels of security, proper configuration is crucial.7
In curbing and mitigating risks, consider the following options.
- Update VPNs, network infrastructure devices, and devices used in working remotely with the latest software patches and security configurations.
- Ensure there is an IT security team prepared and ready to attend to remote access cybersecurity incidents with these functions, but not limited to log review, attack detection, incident response, and recovery.
- Implement Multi-Factor Authentication (MFA) on all VPN connections to increase security. If MFA cannot be implemented, require remote workers to use strong passwords in length and character complexity.4
- Close monitoring of VPN accesses and activities of employees for prompt action in the possible occurrence of an incident.
CyberSOC Africa as a Managed Security Service Provider (MSSP) primarily provides security services (event monitoring, alerting, incident response, amongst other services) to their clients. VPN is a point of vulnerability into the corporate network hence, all suspicious activities should be reported, investigated and subjected to further verification.
A few notable VPN events to monitor include but not limited to:
- Log in from a compromised account
- Multiple failed log in attempts
- Suspicious activities by a remote user
- Multiple password changes of a remote user
1Source: https://simple.m.wikipedia.org/wiki/Virtual_private_network
2Source: https://en.m.wikipedia.org/wiki/Proxy_server
4Source: https://www.us-cert.gov/ncas/alerts/aa20-073a
5Source: https://www.cloudflare.com/learning/access-management/what-is-a-vpn/
6Source: https://nordvpn.com/blog/vpn-vs-proxy/
7Source: https://www.ncp-e.com/fileadmin/pdf/techpapers/NCP-Attack-Vectors-WP.pdf
8 Source https://www.manageengine.com/network-monitoring/vpn-monitoring.html
9Source https://www.plixer.com/blog/how-to-monitor-vpn-traffic/
10Source https://vpnoverview.com/vpn-information/what-is-a-vpn/