Cyber attacks leveraging on the Covid-19 scare Worldwide
CyberSOC Africa is closing the ever-growing gap between cyber needs and the resources to address them by training hundreds of African cyber security specialist annually - and employing the very best of them.
Executive Summary
Threat actors and cybercriminals have been leveraging the hype and fear connected with the growing Coronavirus (COVID-19) pandemic, emergence of various COVID-19 cyber threats have been on the rise using various phishing techniques as a guise of providing information on the COVID-19 virus. The threat actors lure the victims into engaging with each phishing campaign by using branding associated with the Centers for Disease Control and Prevention (CDC) in the United states and the World Health Organization (WHO) to gain the trust of the victim, they also associate with country specific health agencies to make the phishing campaigns more convincing to victims.
Key Findings
-
Cybersecurity researchers released a journal on some phishing mail samples as seen in Figure 1 below, there are reports of criminals taking advantage of COVID-19 situation and masquerading as health service staff and asking to spray houses, as a preventive measure for coronavirus. Various threat actors impersonated Centers for Disease Control and Prevention (CDC). Threat actors send phishing mails, claiming to be from CDC that reference a flu pandemic, the body of the email instructs the user to open an attached Microsoft Office document for details on how to prevent the spread of influenza, aimed at installing malware on victim’s system.
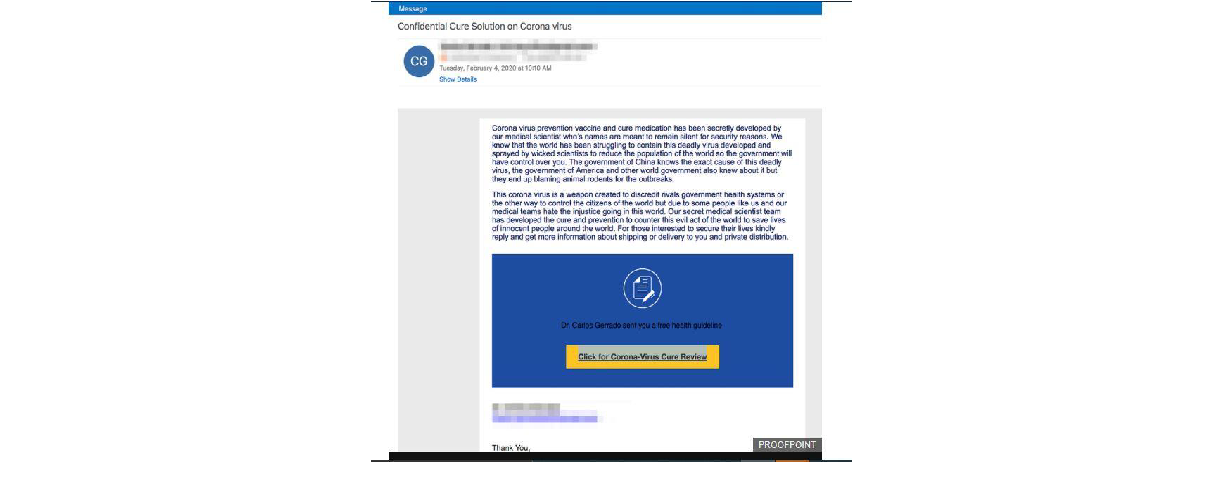
-
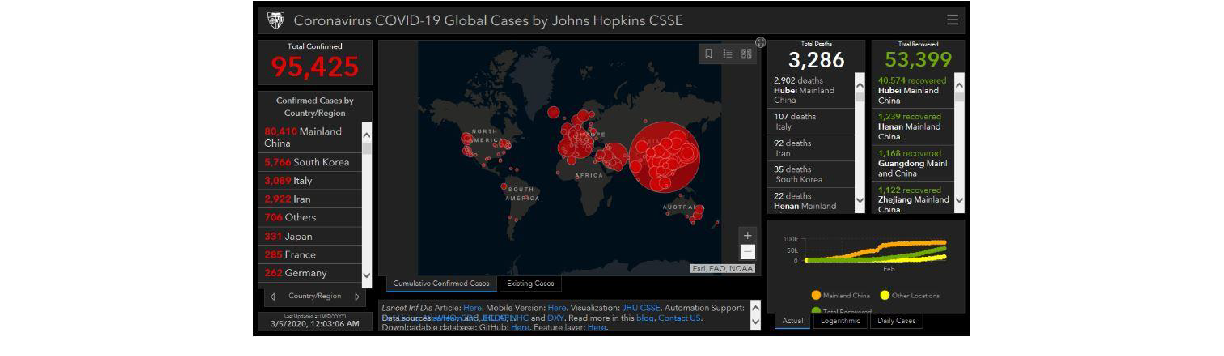
Cybercriminals have also designed a map to mimic a legitimate COVID-19 threat map created by Johns Hopkins University that similarly shows countries hit by the virus together with the latest statistics as seen in Figure 2 below. The malware “AZORult” has a graphical user interface that looks very good and convincing. Once infected with the malware, it downloads additional malwares unto infected system. AZORult creates a new, hidden administrator account on the infected machine in order to allow Remote Desktop Protocol (RDP) connections.
-
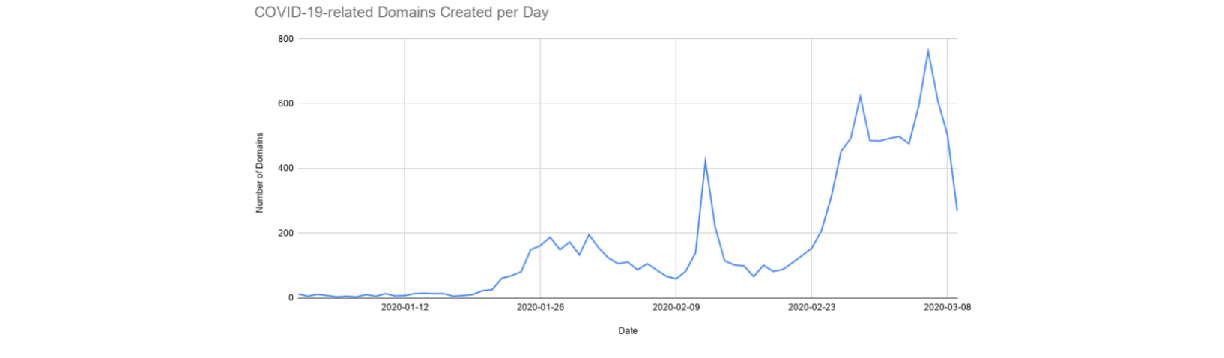
The number of newly registered domains regarding COVID-19 have also been on the increase over the past few month, it has been observed that cybercriminals are creating platform to help support their malicious campaigns as seen in Figure 3 below:
-
Individuals constantly seeking for ways to get help regarding the COVID-19 virus unconsciously visit malicious sites, which download unwanted apps for example “Apps camouflaging as COVID10 Trackers”. This app allegedly runs a ransomware program “CovidLock”, which encrypts victim’s device and requests for certain amount of money, before the device can be used by the user, Figure 4 below, is an example of Lokibot Phishing mail. CovidLock is a type of malware called ransomware, which holds users’ data hostage until they pay a ransom. Ransomware typically targets businesses since they have more money or power to offer. But CovidLock went after individual users, probably in hopes that they would be less suspecting than a company. CovidLock threatened to delete all data from the phone unless users paid $100 in Bitcoin within 48 hours.
In-depth Attack Analysis in Nigeria
Recently, various broadcast messages have been circulating on various social media platforms especially WhatsApp stating that the Federal Government would be giving grants to Nigerian citizens once particular activities have been carried out.
SCENARIO 1
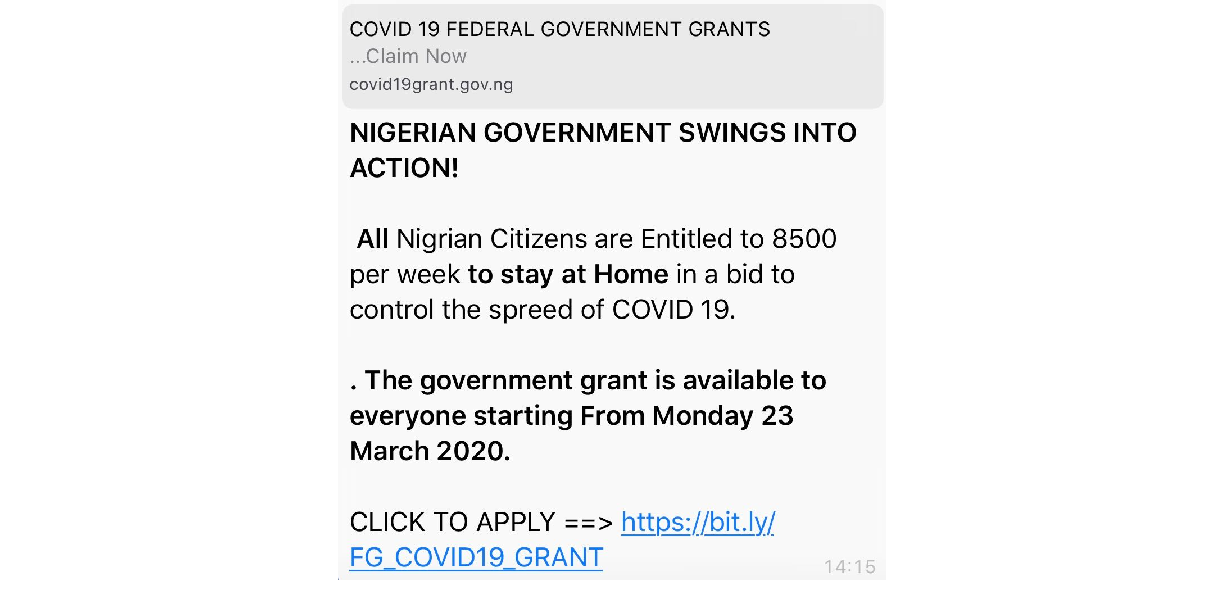
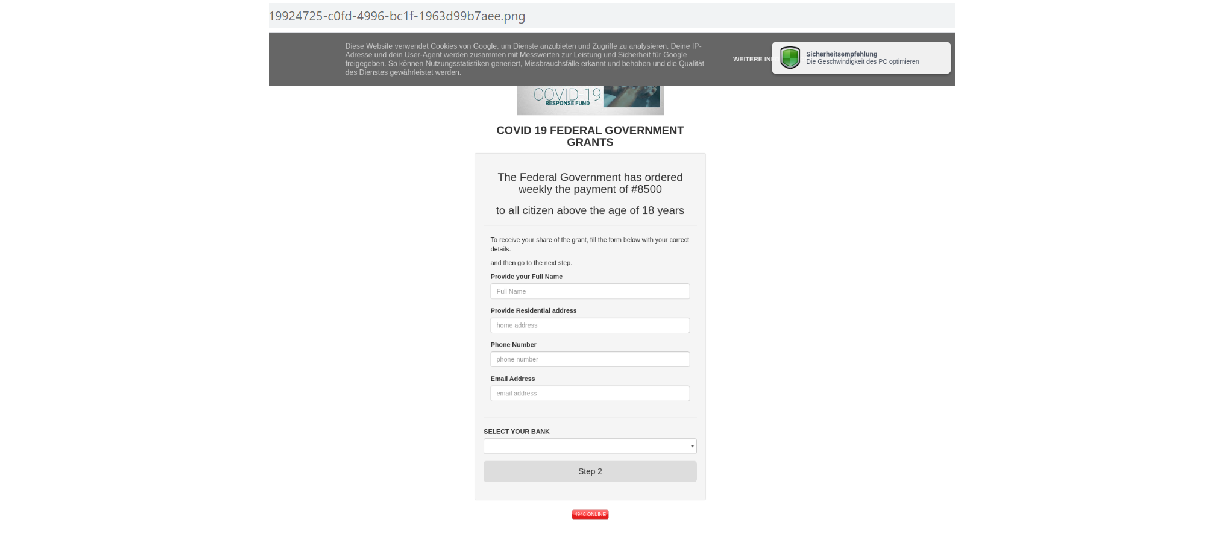
The first WhatsApp message that was discovered to be in circulation was one stating that the Federal Government would be giving each Nigerian citizen a sum of #8500 per week to stay at home to help control the spread of COVID19, the message also contained a link each victim is to click to apply for the grant, a screenshot of the said message is as seen in Figure 5 below:
Once the embedded link in the message “hxxps://bit.ly/FG_COVID19_GRANT” is accessed, it redirects to the URL “covid19-fg-grant.blogspot.com”. The domain contains a form that is to be filled by each victim, supplying personal information regarding about themselves as seen in Figure 6 below:
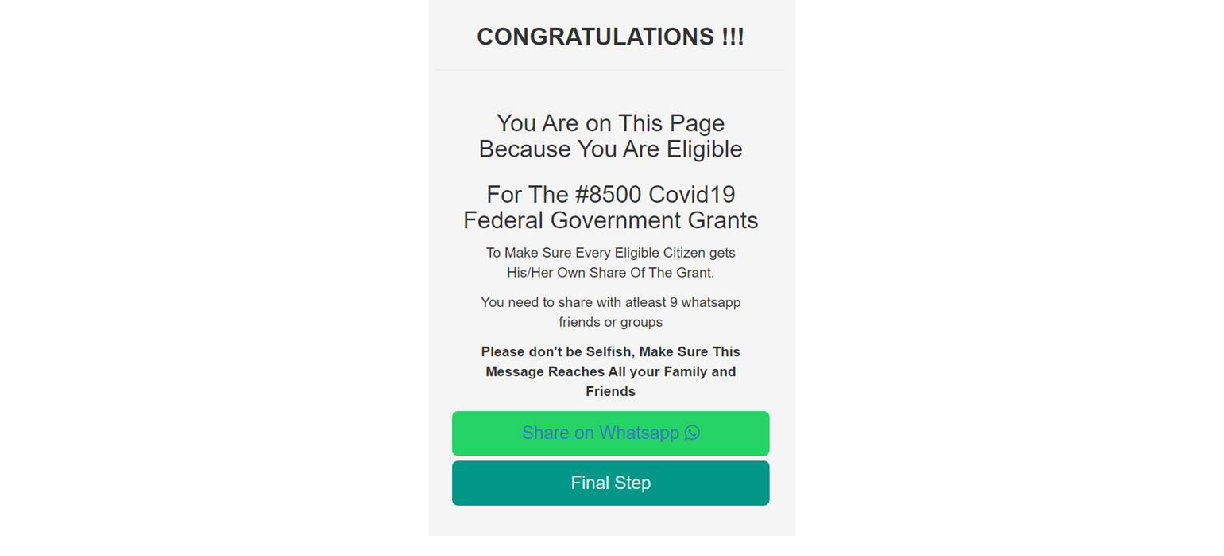
After details have been submitted, a message is seen telling you share with your contacts on WhatsApp to proceed to the final step as seen below:
SCENARIO 2
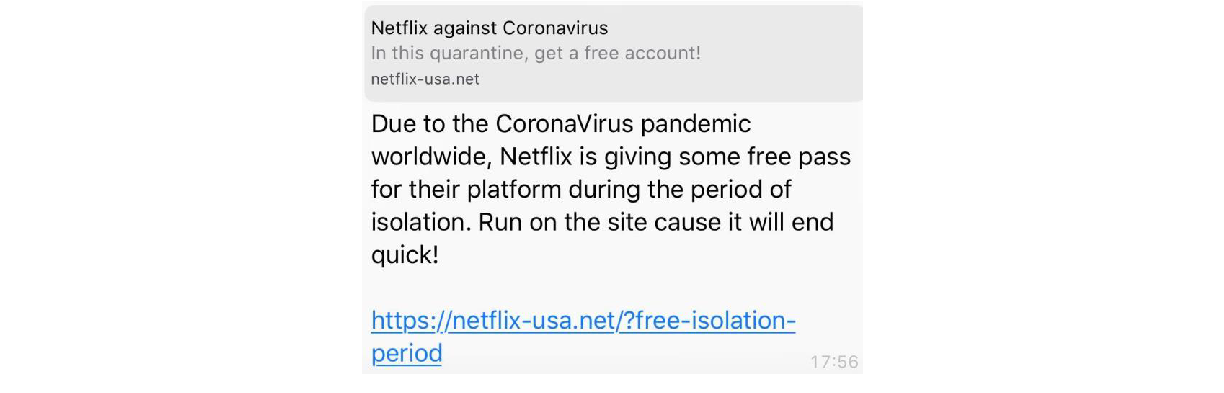
The second broadcast message seen in circulation was one regarding Netflix giving a free pass for selected users to use their platform during the isolation period for free. The message contains a link to give a free pass to Netflix, below in Figure 8 is a screenshot of the message being circulated:
Once the link is accessed, it is initially identified as a phishing site by google that is likely to install a software or get confidential information from victims. Once the warning page is bypassed, it redirects to a page mimicking the Netflix website but also contains Facebook comments as seen in Figure 9 below:
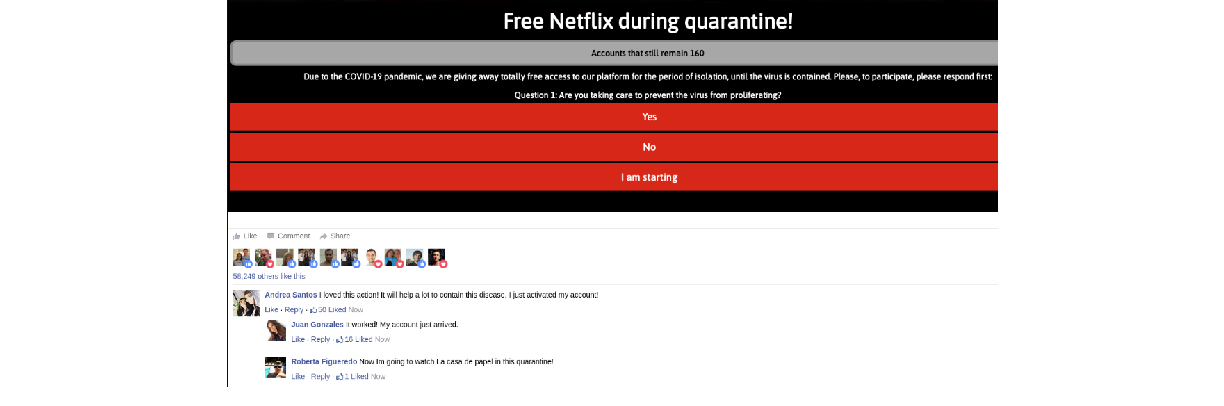
Upon arriving the website, the first course of action to obtaining a free pass to Netflix is by responding to a questionnaire made available. Once the questionnaire has been completed victims are urged to share with 10 of their WhatsApp friends or groups to activate the account as seen in Figure 10 below:
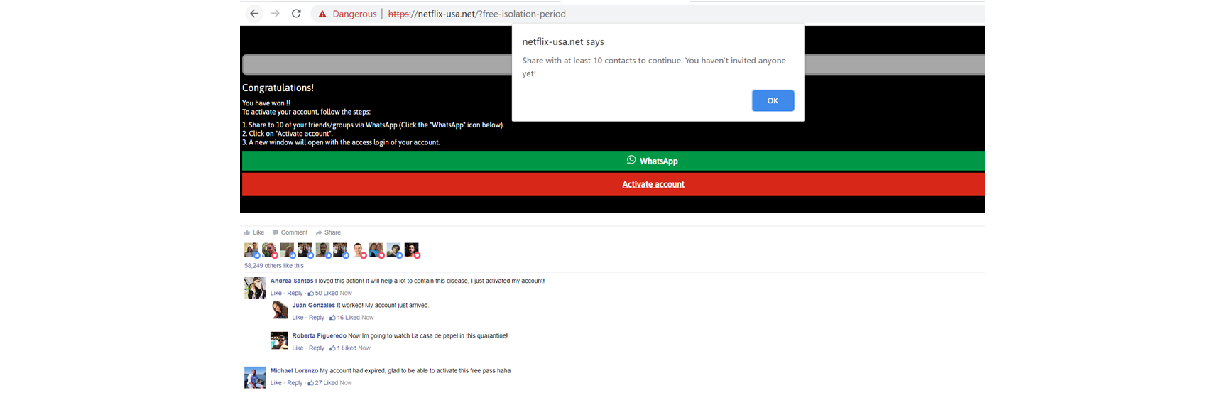
Attempts made to access to the “WhatsApp” link shows the page making attempts to call out to google analytics, it is also observed that attempts are made by the domain to obtain user agents details of the victims access the website.
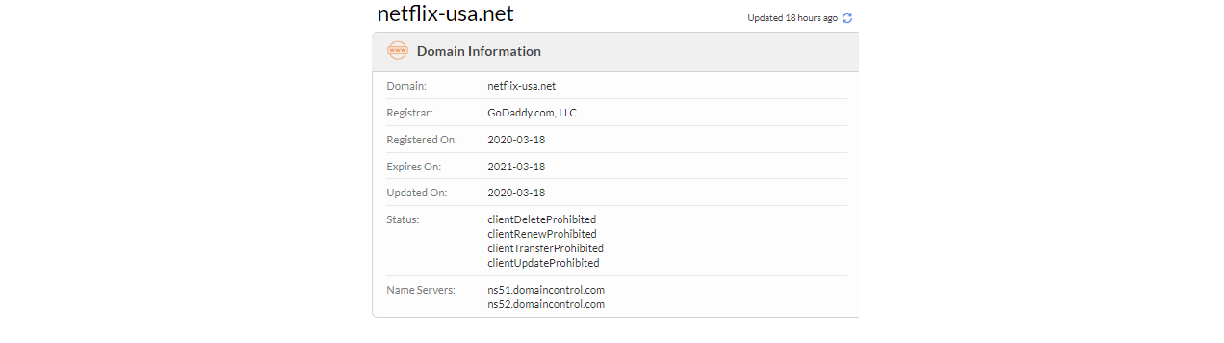
Further investigation on the domain “netflix-usa.net”, revealed that the domain was registered on the 18th of March 2020 and the domain registrar was identified as “Godaddy”, detailed information regarding the domain is as seen in Figure 11 below:
SCENARIO 3
The third broadcast message is similar to scenario 1 in terms of the message also stating that the Federal Government would be paying all Nigerian citizens a sum of #85,000 to stay at home for a period of one month starting from the 30th of March 2020. , The message also contains a link each victim is to click to apply for the grant, a screenshot of the said message is as seen in Figure 12 below:
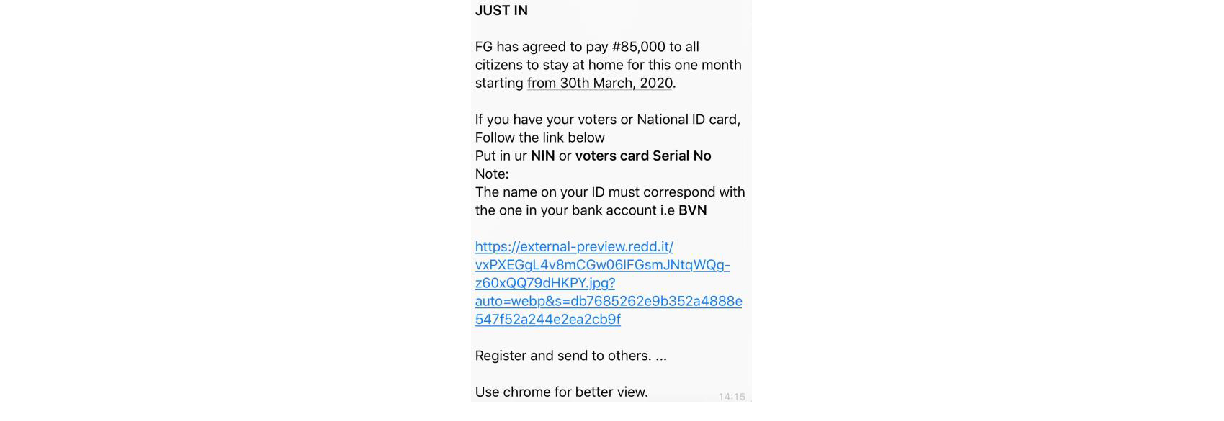
Once the embedded link is access it doesn’t redirect to a form but show an image, a screenshot of the domain is as seen below in Figure 13 below:
Mode(s) of Attack:
- Threat actors sends out phishing mails in different languages, such as English, French, Italian, Japanese, and Turkish. The phishing emails impersonate Individuals such as Doctors, Tax fund officials and the World Health Organizations (W.H.O).
- The Phishing mails contains various malicious links that redirect users to download malicious applications.
- The body of some mails also contains, a link and an executable named “corona-virus- map.com.exe”.
- Victims who visit the page are redirected to a fake and malicious map of the globe highlighting which countries the virus has spread together with statistics on the number of deaths and infections recorded.
- Once the target opens the link, a malware is downloaded on victim’s system, known as “AZORult”. AZORult is an information stealer and was first discovered in 2016. It is used to steal browsing history, cookies, ID/passwords, cryptocurrency and more.
- There are reports of criminals taking advantage of COVID-19 situation and masquerading as health service staff and asking to spray houses, as a preventive measure for coronavirus.
- Various threat actors impersonated Centers for Disease Control and Prevention (CDC). Hackers sends phishing mail, claiming to be from CDC that reference a flu pandemic. The body of the email instructs the user to open an attached Microsoft Office document for details on how to prevent the spread of influenza, aimed at installing malware on victim’s system.
Signs of Infection:
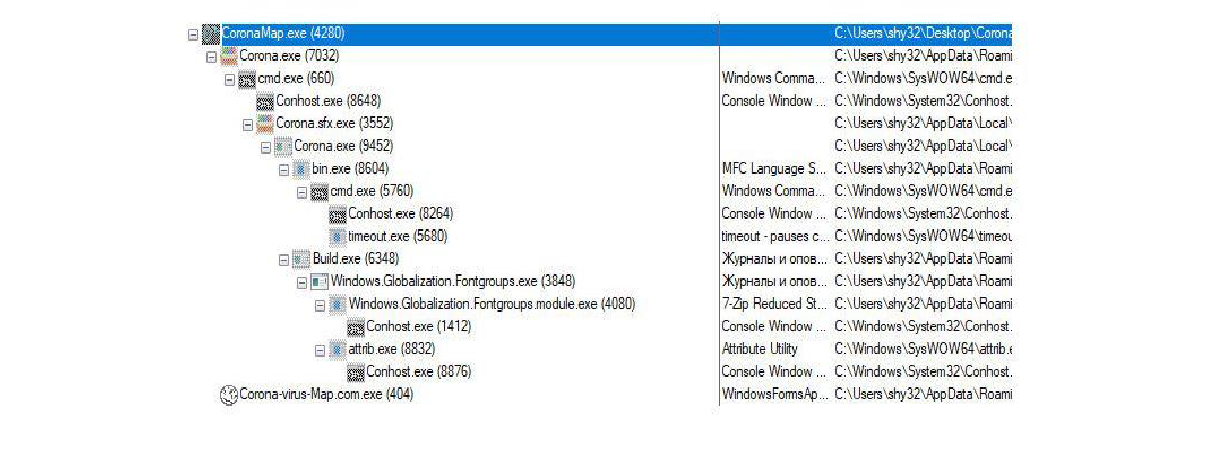
Executing the CoronaMap.com.exe results in the creation of duplicates of the malicious executable and multiple Corona.exe, Bin.exe, Build.exe, and Windows.Globalization.Fontgroups.exe files as seen in Figure 14 below:
Recommendations:
- Disable macros in Microsoft Office for users that do not require it
- Watch out for emails from suspicious sources
- Ensure Antivirus are regularly updated.
- A full system scan should be carried out on all company devices.